WordPress sites can be vulnerable to brute-force login attacks. These can be a drain on the hosting resources and can put your site at risk. However there are some easy steps that can be taken to avoid these attacks and in this post I’m going to review three simple plugins that will help protect your site.
If you have an easy-to-guess password then this can be a massive security hole in your website so it’s vitally important to make sure that you use complex passwords that cannot be guessed, that you don’t use the same password for your website as you use elsewhere and that you don’t share passwords within your organisation. However, even if all your passwords are super-complex, brute force attacks can still drain your site of resources that would be better used serving pages to your visitors.
Often these attacks go unnoticed. However, if you have access to your log files you may well see many lines like this which show multiple attempts to post data into the /wp-login.php page (the default address of the login page for all WordPress sites):
x.x.x.x - - - URI - [29/May/2020:00:33:43 -0400] "POST /wp-login.php HTTP/1.1" 200 5608 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/78.0.3904.108 Safari/537.36" x.x.x.x - - - URI - [29/May/2020:00:33:43 -0400] "POST /wp-login.php HTTP/1.1" 200 5608 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/78.0.3904.108 Safari/537.36" x.x.x.x - - - URI - [29/May/2020:00:33:43 -0400] "POST /wp-login.php HTTP/1.1" 200 5608 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/78.0.3904.108 Safari/537.36"
If you see several of these bunched close together, as in the example above, then it’s often a script working through a dictionary of possible password options.
Unfortunately, WordPress makes it easy for potential hackers to find certain types of information on your site. For example, it will list the authors of blog posts, which can expose the usernames of some users. It also has a very predictable default login URL: /wp-login.php. So any script can try sending a username and password and be confident that it’ll be the login page.
We’ll review three plugins that can help protect your site from these kinds of attacks. However, remember, the first and best form of defence against these kinds of attack is using a good password!
Don’t expose usernames – avoid user enumeration
One easy starting point for hackers is knowing the usernames on your site. Once these are known, hacking can just be a case of trying to guess the password – and there are plenty of scripts that will automate that process.
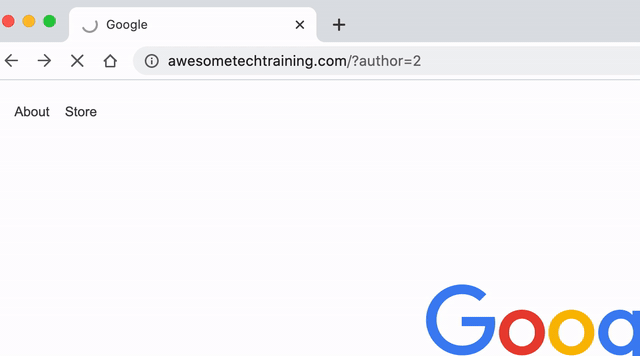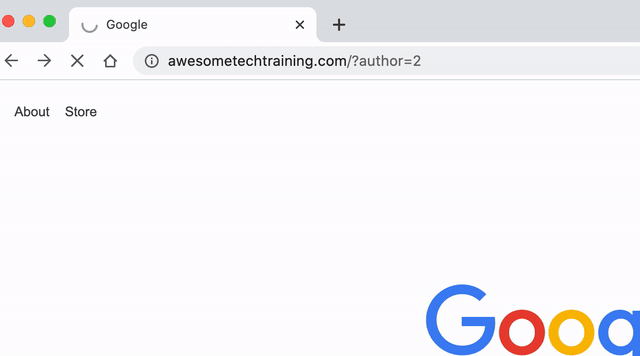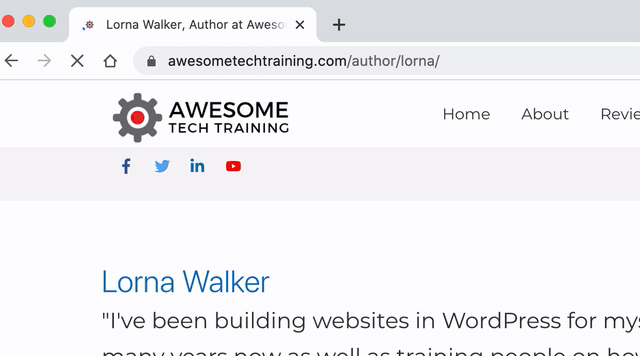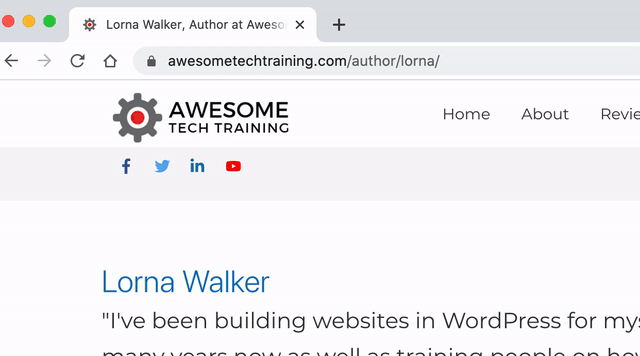
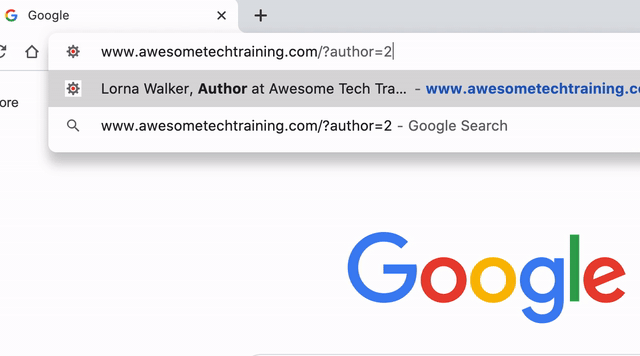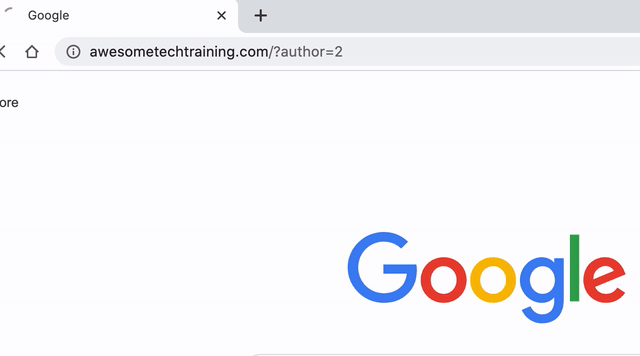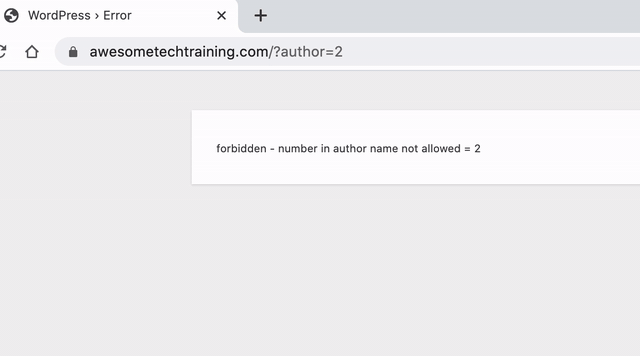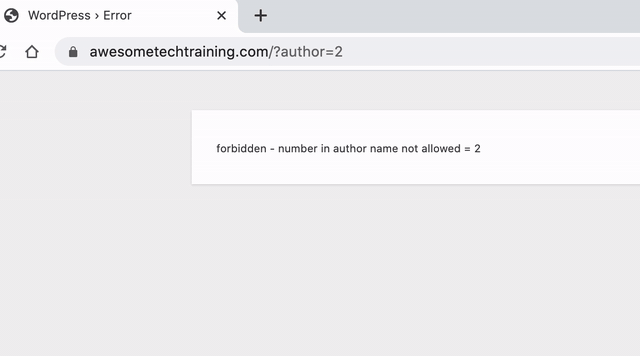
Hackers use a technique called user enumeration to find out the usernames. By adding a numeric user ID to the URL http://www.example.com/?author= it will redirect to a page that lists the user’s posts on the site. All the hacker has to do is run through a series of numbers to try and find all the users on your site.
The GIF below shows what happens when we try checking an author ID on this site. The first URL simply passed the ID “2”, but the site confirms that the user exists and presents us with their username.
To stop this from happening we can use the Stop user enumeration plugin. This plugin simply disables the redirect which links the user ID with the username.
There are just three settings:
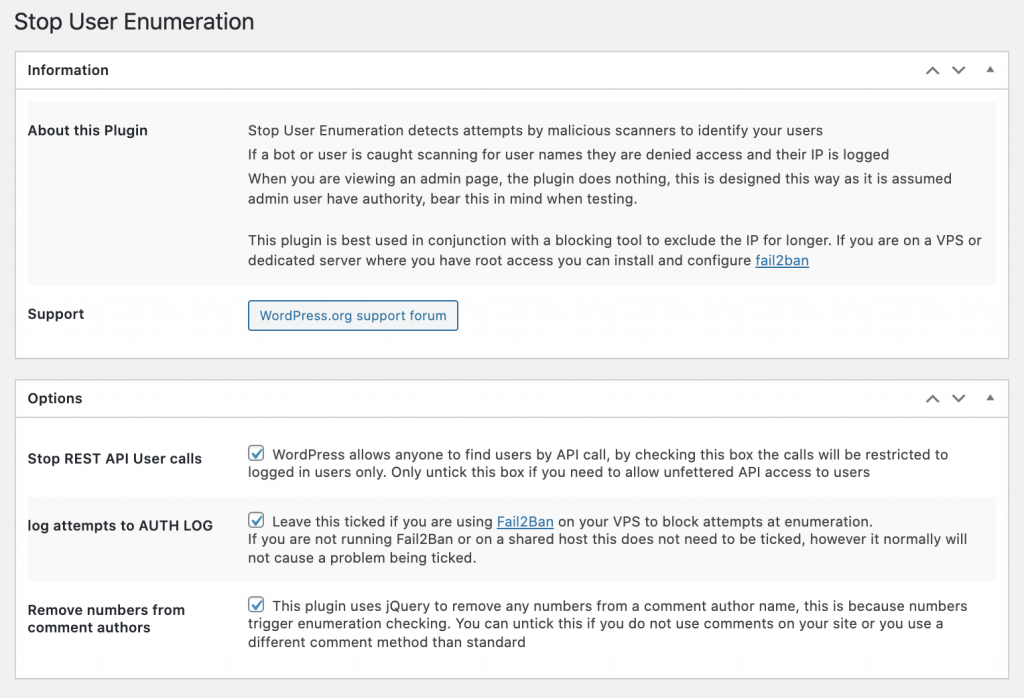
It’s safest to just leave all the checkboxes ticked. Once installed and active, the plugin will show an error page if someone tries to discover a username:
Limit the number of login attempts allowed
Very often the bots that are trying to log into your website will be working through a list of popular passwords. They may try dozens or hundreds of times before giving up and moving to the next site on their list.
You can stop bots (and indeed real people) from trying many passwords by setting a limit to how many times they can guess the password. A good plugin that will help you with this is Limit login attempts reloaded. This plugin will recognise when a user or a bot is repeatedly trying to log in from a single location (IP address) and will block them for a short time before letting them try again. This is enough to repel bots that don’t want to waste time waiting to log in.
Once installed, the settings are straightforward. There is a checkbox to enable GDPR compliance, which means that it will store and use the IP addresses of visitors legally in Europe. You can also set an email address if you want to be notified when users are locked out.
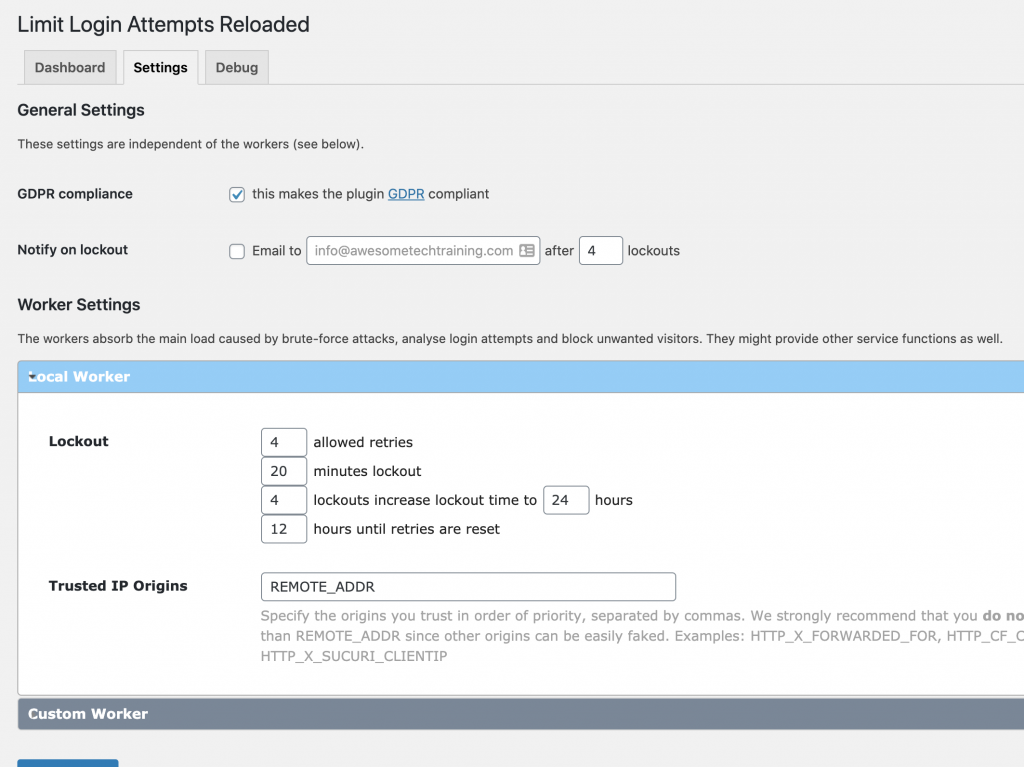
Finally you will find the key settings in the Local worker section which define how the limiting is configured:
- How many times the plugin will let someone try to log in before locking them out
- The number of minutes that the user will be locked out
- A way to increase the waiting time if they are repeatedly locked out – in the example below you’ll see that the default is for a user to wait 24 hours if they are locked out 4 times in a 12 hour period.
When a user enters the wrong login details, they’ll get a warning to say that they only have a few login attempts remaining:
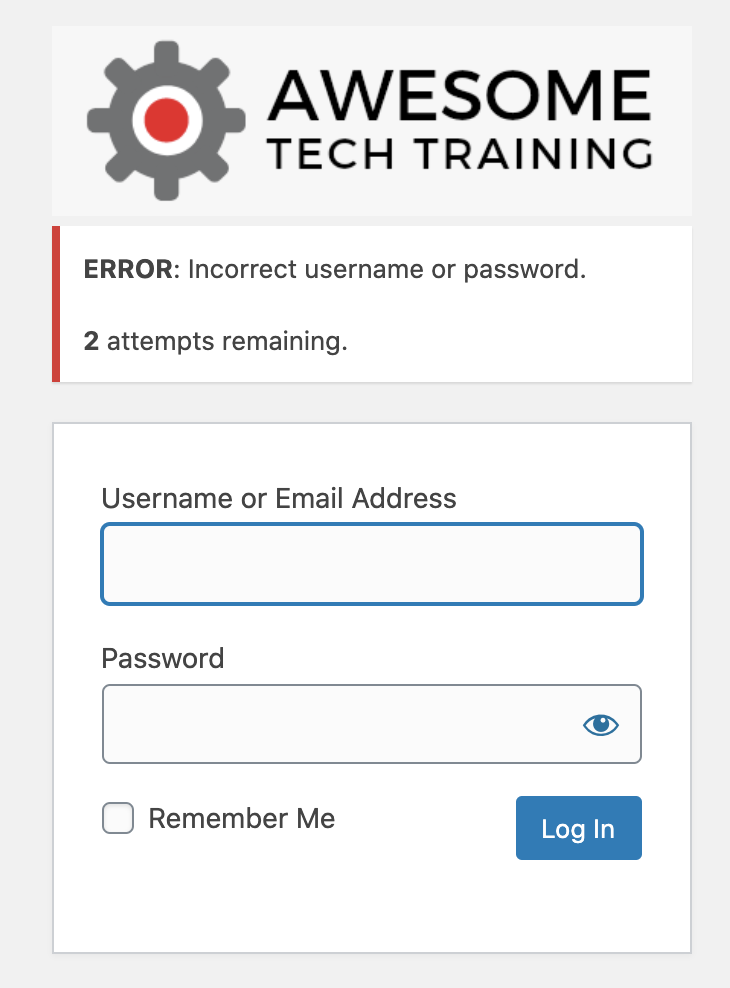
And once locked out, they will get a message saying that they will have to wait before attempting to log in again:
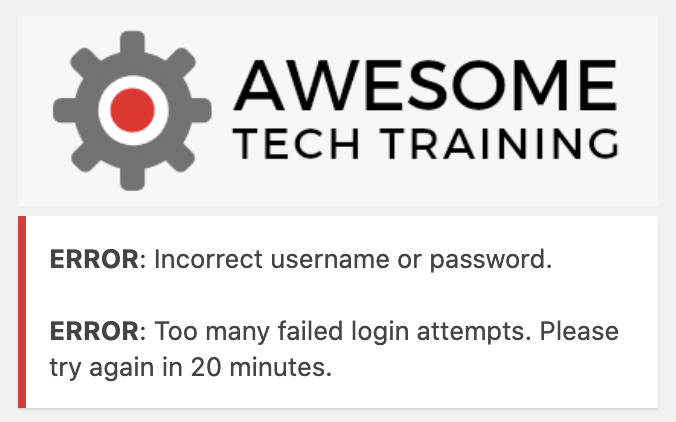
When choosing a plugin you need to consider if your site is using a content delivery network (CDN) or some other proxy that might make it look like all requests are coming from one IP. The limit login attempts reloaded plugin supports CDNs like CloudFlare and StackPath so that you can be certain that bad logins from one person will not affect other users trying to gain access.
Move the login page
A simple yet very powerful way of outsmarting potential hackers is to just move the login page. WordPress has two default ways of getting to the login page, either directly by navigating to /wp-login.php or redirecting from /wp-admin.
If these are no longer available, then your automated attacker will fall at the first hurdle as the page they need to access in order to try logging in will effectively be hidden from them.
We recommend WPS Hide Login when moving a login page. It’s a small plugin that simply changes the login URL. After installing you find the settings at the end of the general settings page:
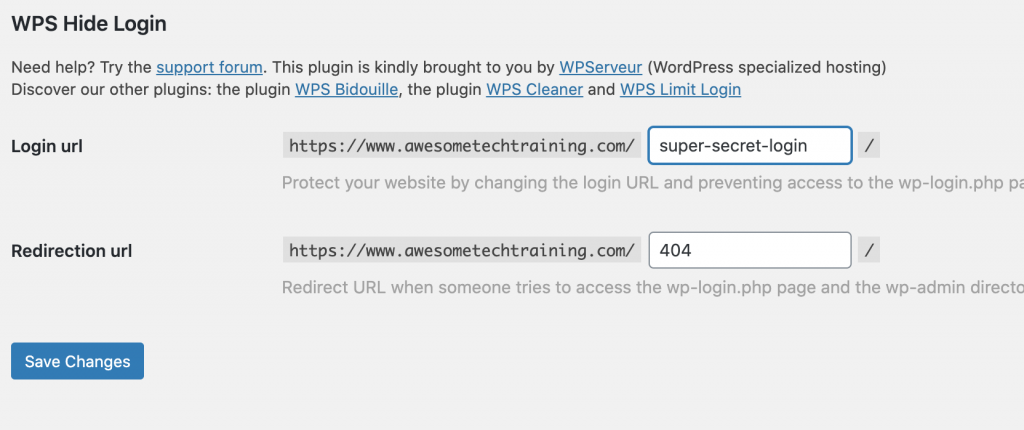
In the example above, the login page will now be found at /super-secret-login rather than /wp-admin. In this way you can stop automated attackers finding their way to your login page.
Remember, if you have multiple users, you’ll also have to make sure that you let them know that the login page has moved and of course you need to make sure you remember the address of the new login page, otherwise you risk being unable to log in to the site yourself.
Other notable mentions
These are just a few simple but very effective ways of making your site login process more secure. There are many other ways out there and these include using a “captcha” to prove that the person logging in isn’t a robot or, as I wrote about in my previous blog, using two-factor authentication.